How to Generate Cyber Security Leads: 10 Effective Strategies
The cybersecurity industry is expected to grow from $152.71 billion in 2018 to $248.26 billion by 2023, at a CAGR of 10.2%. This rapid growth underscores the urgency and massive opportunity for cybersecurity companies to generate leads. But in this competitive landscape, tried-and-true marketing tactics are not enough. Generating cybersecurity leads requires innovative, strategic approaches tailored to this niche B2B market.
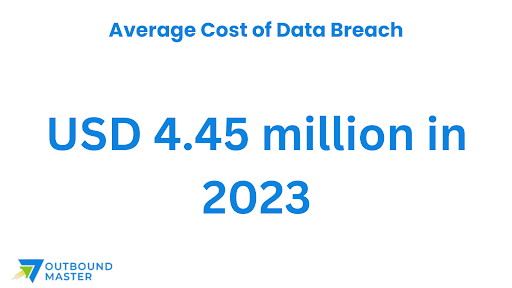
To navigate the complexities of the cybersecurity space and stand out from the competition, here are 10 effective strategies to generate quality leads:
I. Understand Your Target Audience
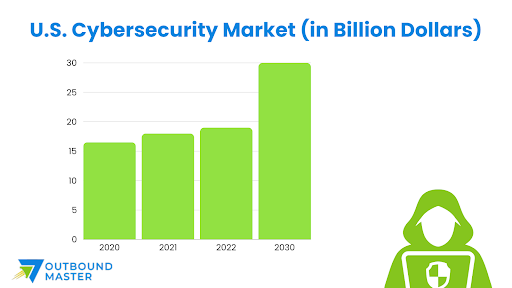
To craft compelling messaging that resonates with potential customers, you must first understand their pain points and needs. Useful segmentation guidelines include:
- Industry: Tailor strategies for SMBs, enterprises, government agencies, healthcare organizations, financial institutions, etc. Make sure to hit your target audience whether it is through account based marketing or multi channel marketing strategy. Each has unique cybersecurity concerns. Targeted lead generation strategies on social media platforms can effectively make more cybersecurity sales.
- Company Size: Solopreneurs have vastly different needs than large enterprises with thousands of employees. Tailored solutions allow decision makers to faster turn to high quality leads.
- Tech Sophistication: Consider the internal technical capabilities of the company to pitch appropriate solutions.
Thorough audience research, surveys, and interviews can reveal common pain points to address in your campaigns. This can also help identify potential leads. For instance, SMBs may struggle with limited budgets and a lack of in-house expertise. Government agencies may require highly specialized solutions to protect classified data. Identifying these insights will allow you to craft targeted messaging.
II. Leverage Content Marketing For Better Cybersecurity leads
| Content-Type | Purpose | Production Effort | Promotion Tactics | Key Metrics |
| Blog Posts | Establish expertise and thought leadership. Target informational keywords. | Low. Can be developed quickly. | SEO optimization, social media, email newsletters. | Views, social shares, backlinks, lead generation |
| Ebooks | In-depth education and lead generation. | High. Requires extensive research and writing. | Landing page, gated download, paid ads. | Downloads generated, email subscribers |
| Webinars | Directly engage and educate prospects through interactive presentations. | Medium. Requires planning, promotion, and speaker prep. | Email campaigns, social media, paid ads. | Registrations, live attendance, and recordings viewed |
Armed with audience insights, engage potential leads with educational content marketing that speaks to their concerns. Useful formats include:
- Educational Content: Whitepapers, e-books, and reports exploring current cyber threats based on cyber security industry growth trends make great lead magnets. For example, a report on the rapid rise of ransomware attacks and prevention best practices.
- Blogging: Regularly posting updates on cyber trends, actionable tips, and case studies establishes thought leadership. Optimize posts for keywords like “cyber security case studies” and “cyber security pain points.” This helps in building brand awareness and gives valuable insights to generate high quality leads while not employing targeted lead generation strategies.
- Webinars: Interactive webinars allow potential leads to engage directly with your expertise. Promote them using “cyber security webinars” keywords.
This content provides value and engenders trust, nurturing leads down the sales funnel.
III. Enhance Your Digital Presence
A strong digital presence is crucial for getting your helpful content and offerings in front of the right audiences. Optimize every digital touchpoint through:
SEO Strategies
- Target informational keywords like “cyber security solutions” in your content to attract people searching for answers.
- Optimize page titles, headers, meta descriptions, alt text, URLs, schema markup, and more for keywords.
- Provide helpful, well-researched content that answers prospects’ questions to build trust and authority.
- Publish new long-form content regularly like blog posts, ebooks, and videos to showcase expertise.
- Ensure site architecture is streamlined for SEO.
- Build backlinks from other reputable sites through guest posting, partnerships, etc.
- Monitor rankings and traffic from organic search.
Social Media Marketing
- Develop LinkedIn and Twitter campaigns with educational cybersecurity content tailored to B2B audiences. This enables your compony to generate cybersecurity leads through social media marketing strategy.
- Join and engage with cybersecurity groups and discussions on social platforms.
- Run LinkedIn ads targeted to specific titles, companies, and interests. Use social media listening tools to know which are the best times to run ads for your leads.
- Partner with relevant influencers to create co-branded social content.
- Promote your new blog posts, webinars, and resources through social posts.
- Analyze social traffic, lead generation, and sales attribution.
Website Optimization
- Ensure the site is mobile-responsive for a seamless experience across devices.
- Include clear calls-to-action for contacting sales, requesting demos, and downloading content.
- Feature seamless lead capture forms tied to your CRM.
- Make site navigation intuitive and pages easy to scan for information.
- Optimize page load speeds for better user experience.
- Set up conversion and user behavior tracking.
Enhancing your digital presence amplifies the impact of your lead generation efforts and ensures you meet cybersecurity buyers whom they already engage online. Continuously track performance from all channels to double down on what works.
IV. Network and Partner Strategically with Cybersecurity Companies
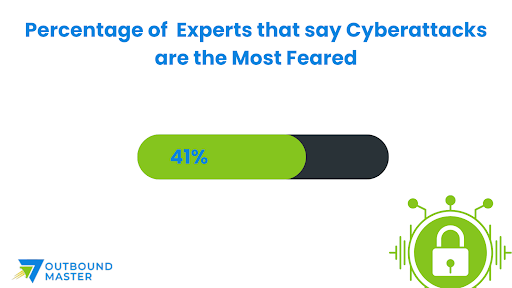
While digital tactics lay the foundation, in-person events and partnerships enable deeper engagement:
- Events: Sponsoring and speaking at industry conferences establishes authority. Attend local association events to connect one-on-one with prospects.
- Partnerships: Co-marketing partnerships with fellow cybersecurity or technology companies can expand reach. This helps prospects along the lead generation processes.
- Influencers: Engage industry analysts, bloggers, and thought leaders to create co-branded assets and content promoting your solutions.
These collaborations develop relationships and trust with qualified prospects already engaged with industry experts.
V. Deploy Paid Advertising
While organic efforts establish brand authority over time, paid advertising allows you to proactively reach interested prospects right when they are searching for cybersecurity solutions. Useful paid strategies include:
PPC Campaigns
- Run Google Ads campaigns focused on commercial keywords like “cyber security marketing strategies” and “managed security services.”
- Create LinkedIn Sponsored Content and Text Ads targeted to specific titles and accounts.
- Leverage Google Display Network to reach audiences browsing content sites.
- Use Google Customer Match to target your email lists and existing contacts.
- Set up remarketing campaigns to re-engage past visitors.
- A/B test ad copy, landing pages, and calls to action.
- Monitor cost-per-click (CPC), click-through rate (CTR), cost-per-lead (CPL), and return on ad spend (ROAS).
Retargeting Ads
- Install tracking pixels company-wide to gather website visitor data.
- Build custom audiences to re-engage leads who previously visited pages but didn’t convert.
- Develop sequenced ads reminding them to download content or contact sales.
- Tailor messaging based on their engagement history.
- A/B test retargeting creatives, offers, and frequencies.
Streaming/Connected TV Ads
- Identify shows and networks popular with your target audience for OTT/CTV ads.
- Run brief 15-30 sec video ads on streaming devices or smart TVs.
- Utilize capabilities like household IP targeting and device ID targeting for accuracy.
Apply rigorous testing processes to optimize paid campaigns and allocate budgets to top-performing platforms driving profitable conversions. This should be able to enhance qualified sales.
VI. Tap Into Email Marketing
| Campaign | Use Case | Segmentation | Key Metrics |
| Educational Drip Campaigns | Nurture cold leads by providing value over time | Industry, company size, lead stage | Open rates, CTR, conversions |
| Targeted Outreach | Send personalized messages addressing needs | Firmographic data, technographic | Opens, replies, meetings booked |
| Time-based Nurture | Guide prospects through the sales funnel | Lead stage, activity data | Unsubscribe rate, sales cycle length |
| Customer Re-engagement | Bring back inactive contacts | Purchase history, LTV | Opens, repeat purchases |
Personalized Outreach
- Segment your email lists by industry, company size, location, and interests.
- Craft targeted emails that speak to specific pain points based on their profile.
- Use dynamic personalization to customize content and offers in emails.
- Send timely follow-ups to re-engage prospects who previously showed interest.
- Track open and click-through rates by segment to optimize outreach.
Lead Nurturing
- Develop automated email nurturing flows tailored to different lead stages.
- Provide multi channel marketing strat to “warm up” prospects over time.
- Use timing triggers to send follow-ups after demo requests.
- Offer limited-time discounts to move leads down the funnel.
- Track unsubscribes and spam complaints to refine messaging.
Curated Newsletters
- Offer curated cybersecurity newsletters with original reporting and analysis.
- Include case studies demonstrating your expertise and successes.
- Promote upcoming events, new content offers, and service updates.
- Share advice columns and Q&As to build relationships.
- A/B test subject lines, content formats, and calls to action.
Compliance
- Acquire explicit consent with a double opt-in process.
- Make unsubscribing easy within every email.
- Carefully monitor blocking and spam complaints.
- Keep email lists cleaned and up-to-date.
- Stay up-to-date with email regulations like the CAN-SPAM Act.
Robust email marketing campaigns aligned to the buyer’s journey can nurture cold prospects into satisfied, high-lifetime-value customers over time. Continuously optimize based on detailed analytics.
VII. Offer Free Tools and Resources
Lower barriers to entry and build trust by offering value upfront:
- Risk Assessments: Provide free network audits, vulnerability scans, and risk assessments, offered in exchange for contact details.
- Free Trials: Let leads test your services firsthand with free trials.
- Checklists: Offer downloadable security checklists for common concerns like data breaches.
These valuable “cyber security free tools” turn interest into measurable leads.
VIII. Launch a Referral Program
Turn happy customers into promoters with referral incentives:
- Satisfied Clients: Follow up with happy clients asking for introductions and referrals to their networks.
- Incentives: Provide discounts, service credits, or commissions to motivate referrals.
Referrals convert at higher rates by coming from trusted sources.
IX. Track and Analyze Performance
Robust analytics should guide your optimization efforts:
- Conversion Tracking: Which strategies deliver the most cyber security leads at the highest conversion rates?
- ROI: Monitor CPA and CPL to assess profitability across initiatives.
- A/B Testing: Test variations in copy, landing pages, offers, and more to incrementally improve performance.
Continuously refine based on data to maximize your lead generation budgets.
X. Forge Partnerships and Alliances
Partnerships with other players in the cybersecurity ecosystem can unlock access to new segments and turn partners’ customers into your leads. Useful partnerships may include:
- MSPs: Partner with managed service providers (MSPs) to offer bundled or integrated services to their SMB customer base.
- Technology Vendors: Coordinate with vendors offering complementary solutions like cloud, networking, or endpoint security to provide an integrated suite.
- Advisory Firms: Collaborate with cybersecurity advisory firms that can recommend and refer your services to their clients. Offer revenue-sharing incentives.
Activating these partners multiplies touchpoints with your target buyers. Cybersecurity firms and cybersecurity professionals are the best ways to collaborate with your cybersecurity company.
By taking an integrated approach that combines content marketing, digital enhancements, strategic partnerships, and analytics you can cut through the noise to connect with potential leads. Tailor messaging to your audiences’ needs, meet them where they already engage online, and build trust over time through valued insights rather than product pitches.
Conclusion
Generating leads in the rapidly growing cybersecurity space requires specialized expertise and strategic marketing. By fine-tuning your targeting, providing promotional and educational content, optimizing digital touchpoints, forging partnerships, deploying multi-channel tactics, and closely tracking performance, cybersecurity companies and cybersecurity firms can stand out and nurture interested prospects into customers. With the right approach, the expansive opportunities in this evolving industry can be captured and converted.
Frequently Asked Questions (FAQs)
What makes cybersecurity lead generation unique?
Cybersecurity is a particularly challenging space for lead generation due to the technical complexity of solutions, long enterprise sales cycles, and the need to establish credibility. Buyers are wary of aggressive sales pitches and desire education. Strategies should focus on helpful content and relationship-building.
How can SMBs compete against big companies?
SMBs can better cater to local and regional mid-sized businesses. With their limited budgets, SMB customers value personalized services from accessible local providers. Lead with your expertise in their needs and highlight your nimble and customized approach.
What are the most important metrics?
Track sales cycle length, lead-to-customer conversion rates, cost per lead, and customer lifetime value. Measure content engagement and sales funnel drop-off. Attribution modeling is critical to assess ROI across strategies.



